v380 IPcam: Hardware Hackz
At SecTalks, blinken ran a Hardware Hacking 101 session where we investigated a Chinese IPcam "WiFi Smart Net Camera" v380.
Some specs:
- 720p video
- IR LED
- 2-way intercom (talk to your pets)
- Pan / tilt (motor)
- Microsd card slot
- ONVIF, or use the gross "V380" app
- Either connects to an access point, or runs its own hotspot
- "Smart" motion detection
- Internet of shit cloud connecting to servers in China without TLS
- Anyka AK3918E system-on-chip
It is sold by different manufacturers under different names, but, as of April 2020, is on sale for £16.47. The box has no manufacturer's name on it. Lots of info on blinken's slides.

Read debug logs via UART #
Pull open the case (the side with the sdcard slot comes off) and expose the guts.
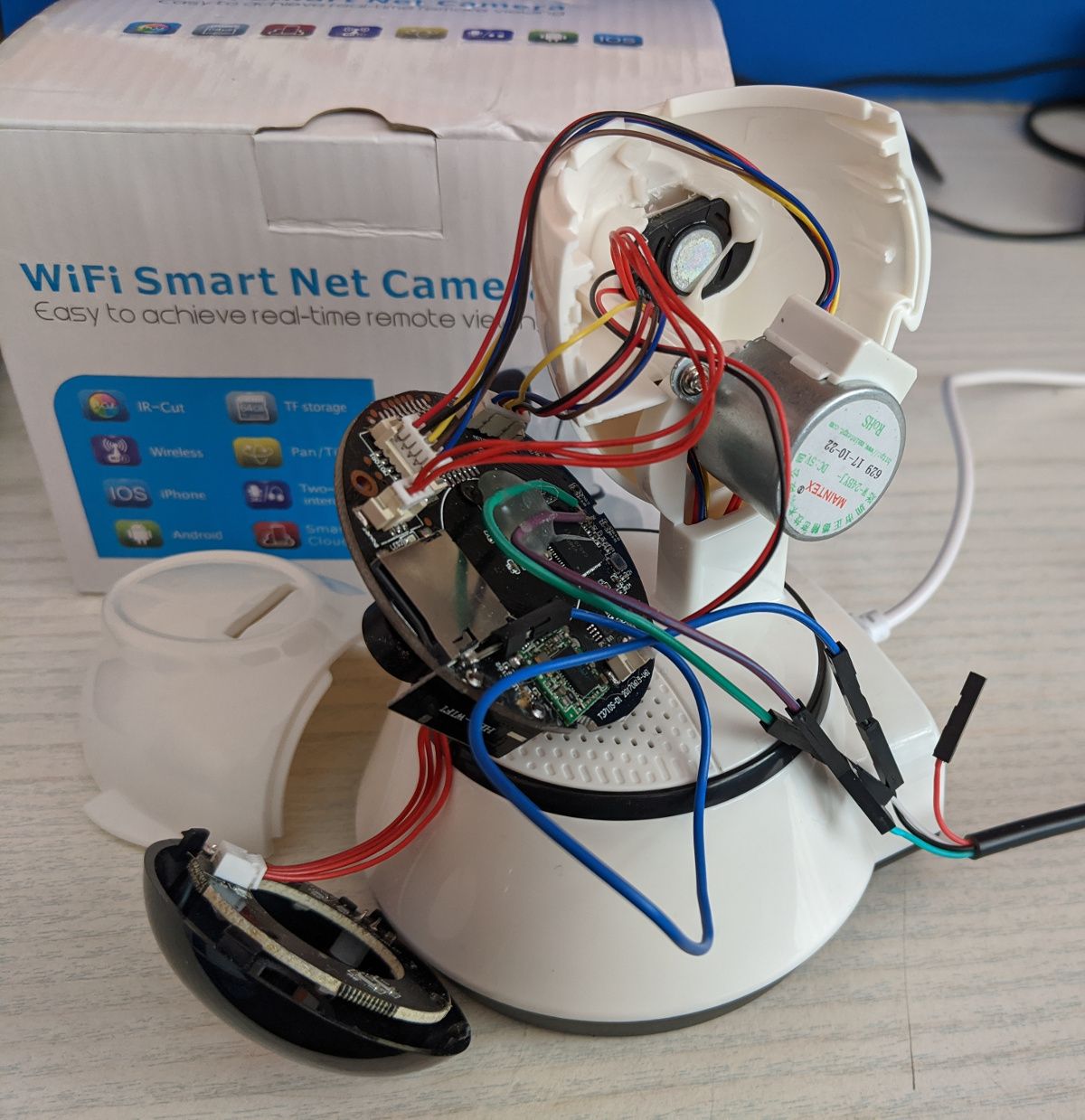
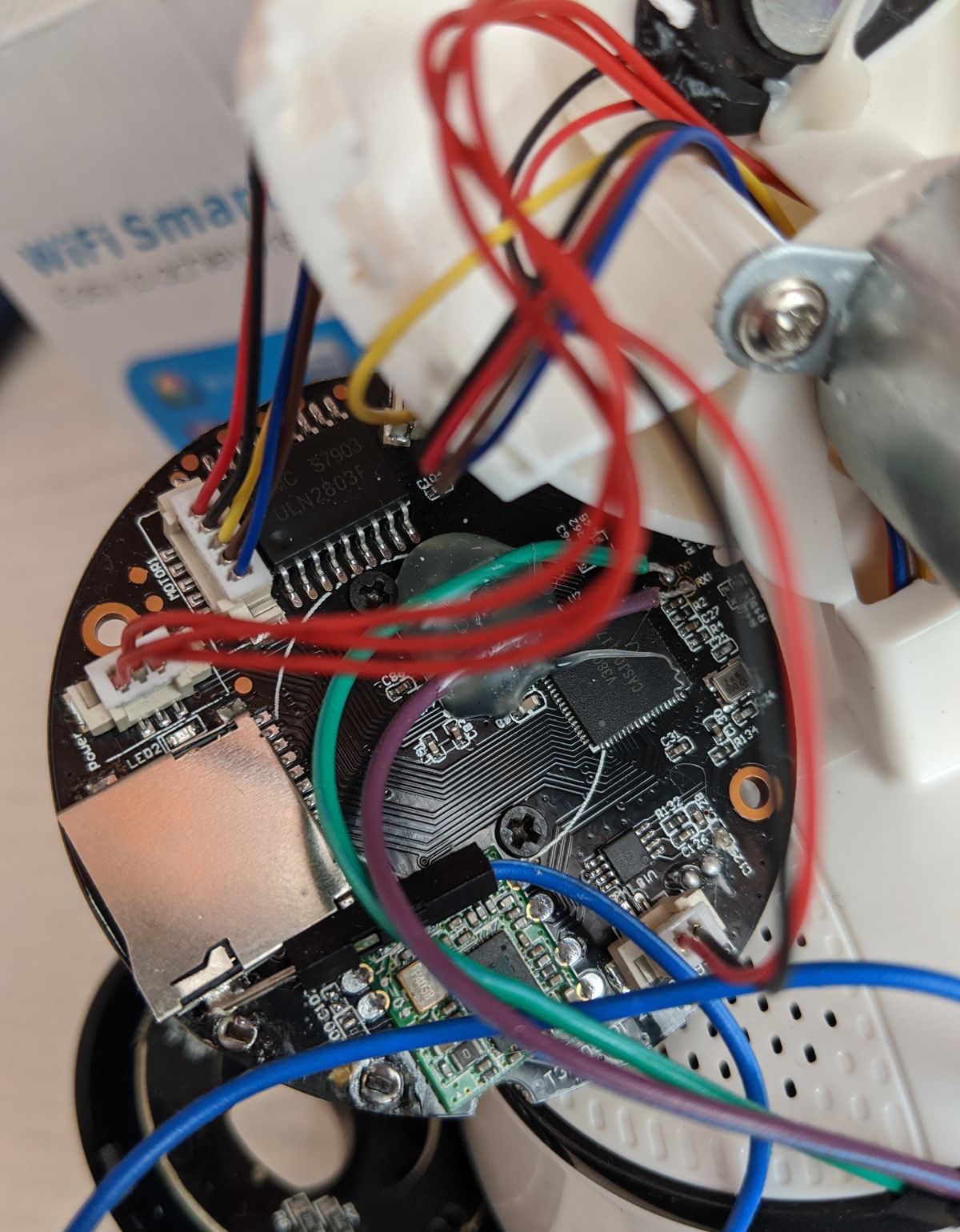

A USB-to-serial cable can be attached to the exposed RS232 serial UART (RX, TX, GND). Connect to it using e.g. sudo screen /dev/ttyUSB0 115200 and power on the camera.
Cloud39E spiboot V1.1.01
load spiflash bios ......
asic clk:60000000, pre-scaler=1 (wanted 20Mhz, got 15Mhz)
the manufacture id is 001720c2
spi param: id=001740ef, total_size=8388608, page_size=256, program_size=16.
erase_size=4096, clock=25000000, flag=0, protect_mask=0.
asic clk:60000000, pre-scaler=1 (wanted 25Mhz, got 15Mhz)
file cnt:4
Read file BIOS
start:560
file len:2095880
ld addr:0x82008000
Load bios from spiflash successfuly!
Uncompressing Linux... done, booting the kernel.
Anyka Linux Kernel Version: 2.1.06
Booting Linux on physical CPU 0
Linux version 3.4.35 (root@lin) (gcc version 4.4.1 (Sourcery G++ Lite 2009q3-67) ) #2 Fri Sep 1 15:13:49 CST 2017
CPU: ARM926EJ-S [41069265] revision 5 (ARMv5TEJ), cr=00053177
CPU: VIVT data cache, VIVT instruction cache
Machine: Cloud39E_AK3918E+H42_V1.0.2
Memory policy: ECC disabled, Data cache writeback
ANYKA CPU AK3916 (ID 0x20150200)
...
V380E login:Lots of juicy info here, the ability to monitor what's going on as you interact with the camera, and the chance to login as root (I don't know the password yet though).
Ports, V380 Android app #
Ports 5050, 5051, 8800 and 8899 are open according to nmap.
Not sure what protocol the app uses to talk to the camera, but it all happens on port 8800. The app logic is mainly in native code, so reverse engineering will be annoying.
One day I might play around a bit more.
- Previous: Pebble Bike Sharer
- Next: Avoiding injection with taint analysis